Security & privacy go hand in hand
Govern together. Eliminate overlap. Optimize workflows.

Trusted by privacy teams at leading organizations













Automation
Dynamic, fully-automated questionnaires
Advanced, customizable questionnaires let you collect detailed information about business activities through a single form. They automatically generate linked processing activities, associated risks, business impact assessments (BIAs), TOMs/mitigations, tasks, and map everything to the appropriate controls.

Flexibility
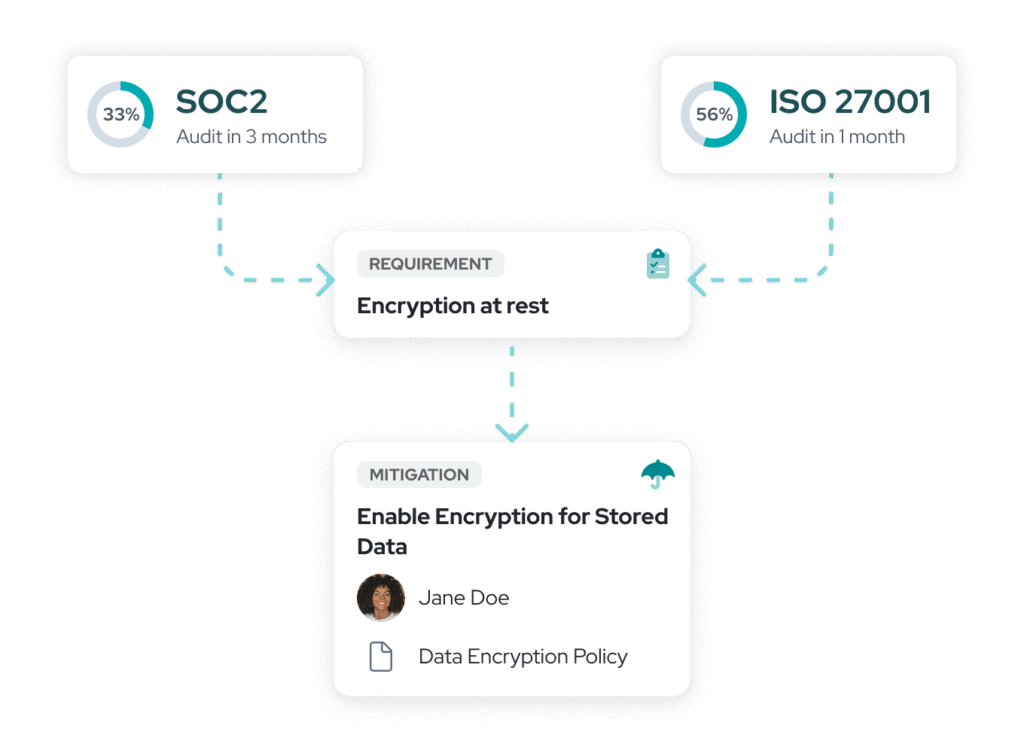
Framework overlap management
Seamlessly share critical information such as risks, vendors, policies, and information systems within your organization in a centralized, up-to-date location. Streamline documentation across multiple InfoSec frameworks by eliminating duplicate evidence, risks, and maintenance efforts.
Audit ready
Risk management, treatment, and register
- Customize your own risk matrix and classify risks based on both initial and residual impact—making it easy to identify those that require immediate attention.
- Define threats, vulnerabilities, mitigations, ownership, and tasks, and track their status to ensure continuous follow-up on risk reduction efforts.
- Seamlessly link relevant elements across your organization—such as vendors, information systems, policies, processing activities, and assessments—to gain a comprehensive view of where risks exist and what controls are in place to mitigate them.


Planning
Powerful compliance roadmaps
Automated ownership & review:
- Assign clear ownership to controls, evidence, risks, mitigations, and more.
- The system automatically detects when reviews are due or when potential non-compliances arise.
- Easily generate tasks from findings, organize them into actionable roadmaps, and manage everything visually with a Kanban board
Everything you need in one place

ISO 27001, SOC2, and more
Built-in frameworks you can start using immediately. Plus the flexibility to bring your own.

Always audit-ready
Configure dedicated auditor views that show only what’s relevant. No clutter, no risk.

Full ownership & review automation
Advanced ownership controls to easily follow up on periodic reviews, without manual upkeep.

Eliminate double work
Share one database of Vendors, IM Systems, Tasks, Risks, Mitigations, Policies, and more between Privacy, Security, Risk, AI, and other compliance teams.

Strategic compliance planning
Use roadmaps to bundle tasks into manageable phases. Stay aligned on progress, deadlines, and scope.

Tailor Responsum to your needs
Highly customizable, designed to support even the most niche requirements with clarity and ease.

In-depth risk management
Capture threat treatment and track risk levels pre and post mitigation with powerful reporting and automation to identify key risks at a glance.

Integrated check-off
Automate periodic agreement of policies and other relevant material with powerful reporting and full traceability.

Version history, forever
Every change is logged. Know exactly who changed what, when, and why.
Security management FAQs
What is security management in data protection?
Why is security management important for GDPR?
What are examples of security controls in privacy programs?
How do you assess data security risks?
Who is responsible for managing data security?
How often should security measures be reviewed?
What is the connection between security and privacy management?
Ready to streamline your security workflows?
Try Responsum free and see how a unified platform simplifies compliance, strengthens risk oversight, and accelerates collaboration between security and privacy teams.





