DORA compliance, controlled & provable
- Centralize ICT risk and resilience
- Manage incidents, testing, and vendors
- Stay prepared for regulatory review

Trusted by privacy teams at leading organizations














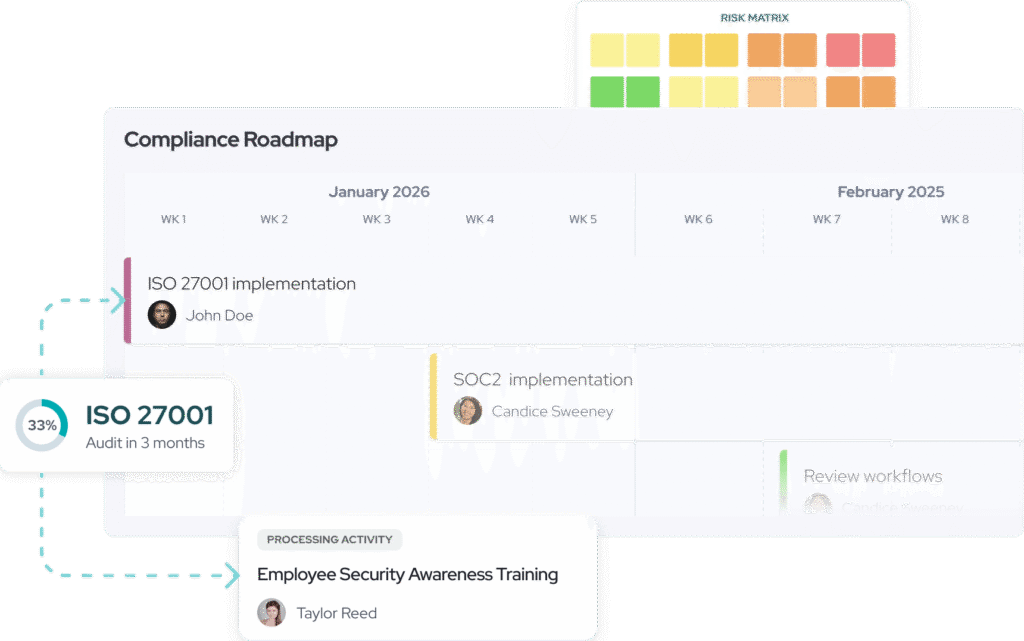
Run DORA as an operational process
Responsum helps financial entities manage DORA requirements with clear workflows for ICT risk, resilience, and oversight.
ICT risk management
Identify and control operational risks
Document ICT assets, risks, and controls in one system. Maintain traceability across your DORA framework.
Incident management
From detection to reporting
Track ICT-related incidents with structured workflows. Prepare consistent documentation for regulatory reporting.
Operational resilience testing
Prove systems withstand disruption
Plan, track, and document resilience tests. Link results to risks and remediation actions.
Third-party oversight
Visibility into critical vendors
Assess and monitor ICT third-party risk. Maintain evidence for contractual and oversight obligations.

Case Study
How Brussels Airport Took Privacy Management to New Heights
Discover how Brussels Airport Company streamlined privacy operations, boosted team collaboration, and gained full oversight by centralizing their privacy management with Responsum.

Cut Through the Noise
DORA demystified
DORA spans thousands of pages across one regulation and five technical standards. Responsum simplifies the complexity with mapped controls, document templates, and clear guidance. Know exactly what to do and where to start.
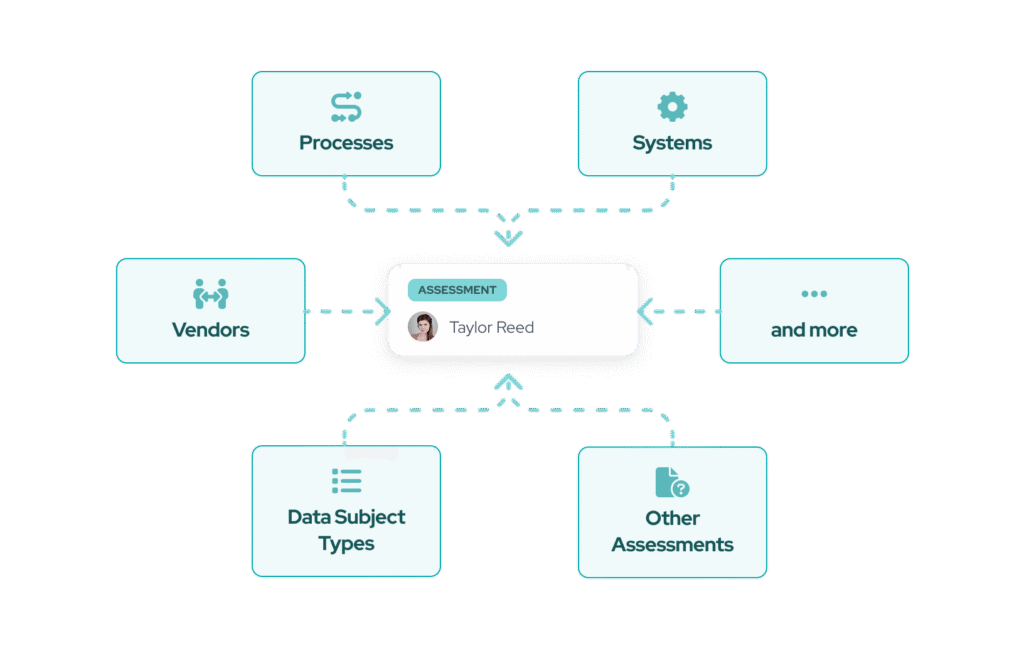
Work smarter
Automate DORA and avoid costly fines
Responsum automates key DORA requirements across systems, vendors, and internal policies. Get real-time visibility into your compliance posture and reduce manual work—so you’re ready every day, not just at audit time.
Stay in control
Adaptive scoping for complex environments
Define and adjust which systems, vendors, and processes fall under DORA. Whether you’re setting up or scaling, Responsum helps you focus on what matters and adapt as your operations evolve.
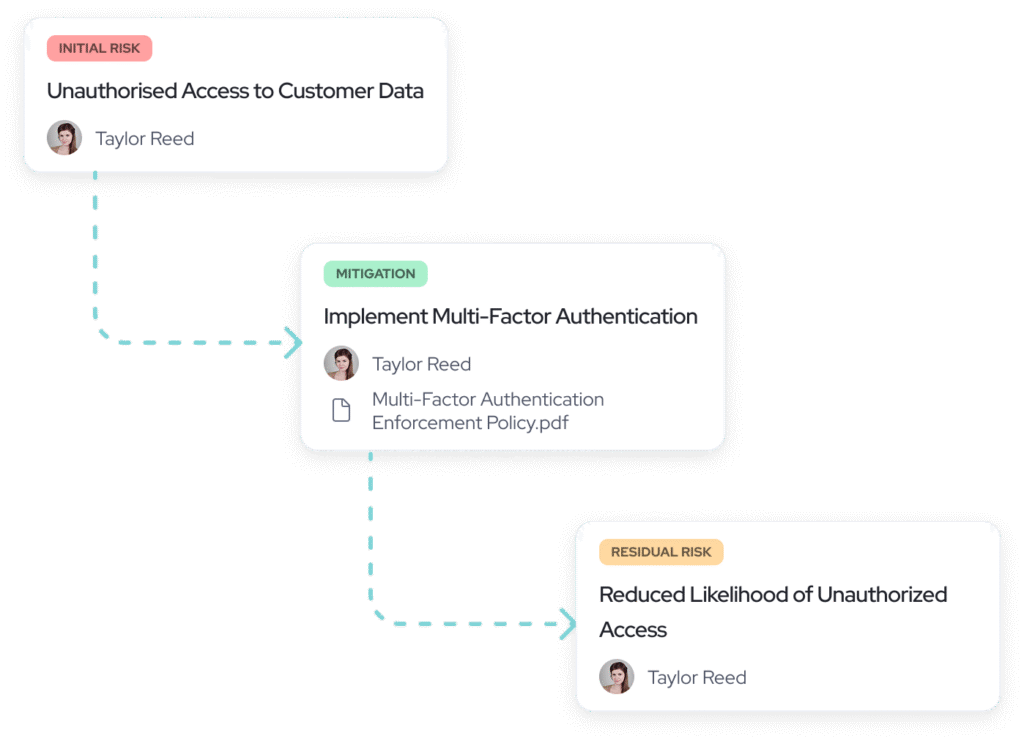
Everything you need for DORA
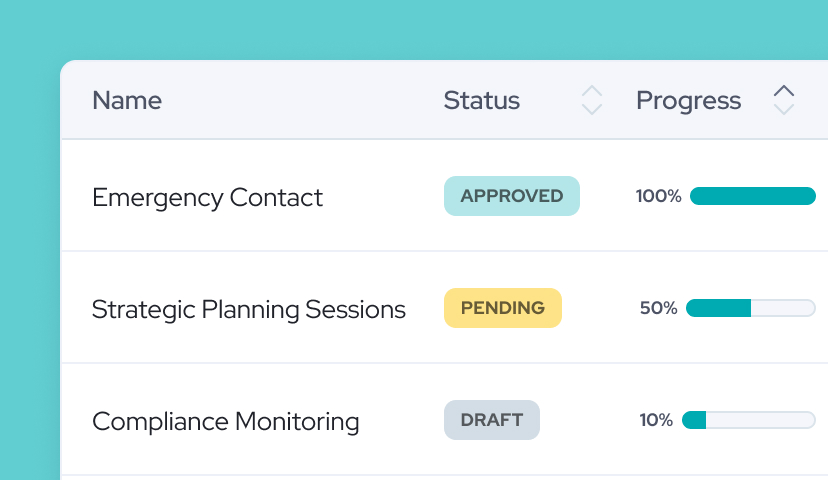
ICT Asset Inventory
Maintain a clear register of systems, services, and dependencies.

Risk Assessments
Evaluate impact and likelihood for ICT-related risks.

Control Framework
Define and manage controls aligned with DORA requirements.

Incident Workflows
Log, investigate, and resolve ICT incidents consistently.

Resilience Testing
Document testing plans, results, and follow-up actions.
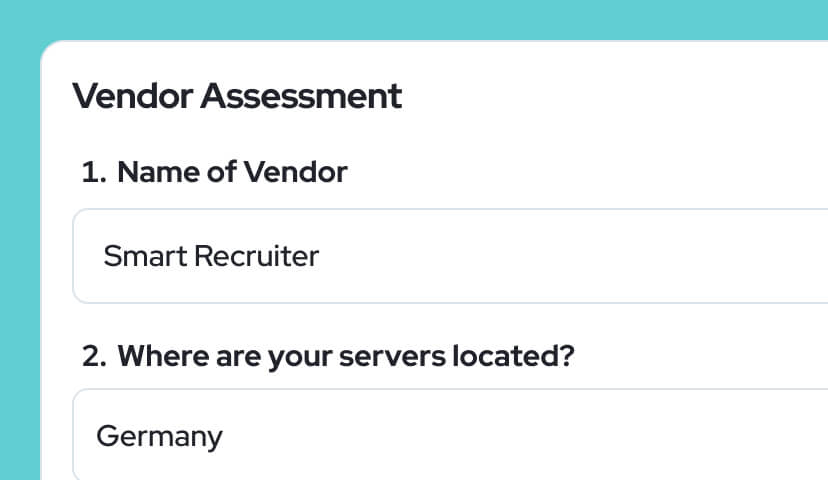
Third-Party Risk
Assess vendors supporting critical functions.

Evidence Management
Store and link documentation across all DORA domains.

Reporting Readiness
Prepare structured outputs for regulators and auditors.

Continuous Oversight
Monitor status and gaps across your DORA program.
Seamless migration from any tool
- Onboarding and migration typically completed within 1 day to 8 weeks, depending on complexity
- Compatible with any setup, whether you're switching from Excel, OneTrust, or another tool
- Included in all pricing packages, with hands-on employee training to ensure a confident start

DORA compliance software FAQs
What is DORA compliance software?
Who must comply with DORA?
What are the main requirements under DORA?
Does DORA require incident reporting?
How does DORA affect third-party risk management?
Can DORA compliance be managed alongside other frameworks?
How does software simplify DORA implementation?
Ready to operationalize DORA?
Ready to experience the power of Responsum? Take the first step toward structured digital resilience by trying Responsum for free today. Get hands-on with a clear platform built for ongoing regulatory compliance.





